So you’ve got a hash and you want to crack it. We’ve already covered a quick way to get to a windows password here but in that example we simply used john the ripper to crack the password… but what if john is taking ages? Step in rainbow tables.
I wont go into detail of what Rainbow tables are as they are already well documented on the web but as a quick summary they are simply pre computed hashes stored in usually large tables in order to tradeoff the CPU/storage issue computers are always up against.
Lets just say we have the hash:
1 | Administrator:500:1d9321d6da8213bdc4482861fc3ea9db:80290fc9b3c2b233769aa9d6ced8bc86::: |
The first, and most common tool, that we’ll use to perform the cracking is ophcrack. It’s easy to install, on debian boxes it’s as easy as apt-get install ophcrack(you’ll need the correct repository).
Once you’ve got ophcrack install you’ll also need to download the rainbow tables for it, they can be found here.
Simply load it up and click the tables icon, you then need to click install in order to load your tables (XP free fast and XP free small):
Then click Load–>Single Hash:
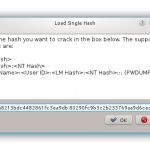
Then it’s as simple as clicking Crack, if the password is found it’ll be displayed as such, simple!
The next tool on the list is rcracki (or rcracki_mt as it’s now known). This tool is to be used with the rainbow tables provided on freerainbowtables.com. The tables are pretty large and for LanManager hashes like we’ve got here you have 2 options:
- lm_all-space#1-7: 34 GB
- lm_lm-frt-cp437-850#1-7: 365 GB
In the example here we’ll be using the lm_all-space#1-7 tables but feel free if you have the time, bandwidth and storage to download both.
Once you’ve downloaded the tables you need to run rcrack_mt and point it towards both the hash and the tables. In this example I’ve dropped the hash used above in hash.txt:
1 2 3 4 5 6 7 8 9 | phillips321@KubuntuDesktop:$ ./rcracki_mt -f hash.txt lm_all-space/*.rti2 Using 1 threads for pre-calculation and false alarm checking... Found 80 rainbowtable files... lm_all-space#1-7_0_10000x51209963_distrrtgen[p][i]_19.rti2 Chain Position is now 51209963 307259778 bytes read, disk access time: 2.33s searching for 2 hashes... cryptanalysis time: 37.33 s |
Depending on where the password falls within the rainbow tables the next bit could take a while…in my case this took ~70seconds on my machine.
1 2 3 4 5 6 7 8 9 10 11 12 13 | statistics ------------------------------------------------------- plaintext found: 2 of 2(100.00%) total disk access time: 74.48s total cryptanalysis time: 11.10s total pre-calculation time: 55.06s total chain walk step: 149955003 total false alarm: 7769 total chain walk step due to false alarm: 29230562 result ------------------------------------------------------- Administrator hacmebank hex:6861636d6562616e6b phillips321@KubuntuDesktop:$ |
And there you have it, two ways to crack a LM hash using rainbow tables.
Leave a Reply
You must be logged in to post a comment.