So I’ve been out of the GPU cracking game for a while as I’ve been running a MacBook on OS X.
After doing a little digging tonight and reading up on the latest version of hashcat (v3.00) it became apparent to me that hashcat now runs on OS X platforms. At last! Thanks to @hashcat (atom) for making the software open source!
For those of you wanting to get… Continue reading
OK, so at my work place we’ve just got some new laptops and they have a proper GPU for a change (we’ve in the past had intel GPUs). I was lucky enough (or unlucky enough) to be given the job of spec’ing these laptops and my hunt was to include a decent GPU for hash cracking. I strived for an ATI chip but with budget in mind and with the… Continue reading
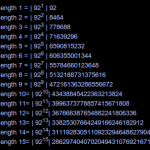
Quiet often people ask me to bruteforce a hash for them. My usual response after the obligatory; where did you get the hash from? is “I’ll run a few dictionaries against it unless you provide me with a charset and length!”
For those that don’t understand it needs to be made clear exactly what bruteforce cracking means.
Lets just say we have a four character pin that can only… Continue reading
We need to capture the WPA 4 way handshake in order to perform an offline GPU attack. For this demo we’ll be using an Alfa AWUS036H wireless card under Backtrack 5 R2 64bit.
Now I could go in depth about capturing the WPA handshake manually using aircrack-ng but it has been covered in full in many places already, so instead im going to use a great python tool call… Continue reading
The tool we’re going to use here is hashcat. I’ll be testing this using a ATI 6950 2GB GPU running on Kubuntu 64bit using catalyst drivers 12.2. Your mileage might vary depending on what card you’re using. Hashcat (now known as oclhashcat-plus) comes with a few different binaries depending on what architecture you’ll be running it on.
- nVidia 32bit – use
- nVidia 64bit – use
- ATI 32bit –… Continue reading