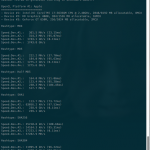
So I’ve been out of the GPU cracking game for a while as I’ve been running a MacBook on OS X.
After doing a little digging tonight and reading up on the latest version of hashcat (v3.00) it became apparent to me that hashcat now runs on OS X platforms. At last! Thanks to @hashcat (atom) for making the software open source!
For those of you wanting to get… Continue reading
So I noticed whilst web app testing that would receive a cookie with a value called bIPs: 709aed354747fda133a5da28dbed60e7 95eb48ad7eae5c0aa9766f0258ae8a35
Looks like it’s using a big IP load balancer. I noticed it was MD5 and that was confirmed by finding the code that generates the hash(cheers scriptmonkey).
I decided to use Hashcat to do the bruteforcing. First thing that came to mind was how to use a dictionary containing… Continue reading
We need to capture the WPA 4 way handshake in order to perform an offline GPU attack. For this demo we’ll be using an Alfa AWUS036H wireless card under Backtrack 5 R2 64bit.
Now I could go in depth about capturing the WPA handshake manually using aircrack-ng but it has been covered in full in many places already, so instead im going to use a great python tool call… Continue reading